LDAP and AD Authentication
Estimated reading time: 7 minutes
This page provides an overview of LDAP and AD Authentication configuration in OT Link Platform.
Overview
Each OT Link Platform instance contains a default user registry for authentication and authorization. OT Link Platform LDAP and AD settings allow you to integrate the OT Link Platform login system with an external authentication registry. For example, this external registry might be the username and password combinations for your company network.
OT Link Platform Supports:
- Active Directory (AD).
- LDAP directories using the RFC2307/2307bis schema.
- Other LDAP directories are supported via direct attribute mapping.
What is LDAP?
Lightweight Directory Access Protocol (LDAP) provides centralized services for login authentication and storage / access of usernames and passwords within a network directory. LDAP uses group mechanisms to facilitate user authentication management. The Active Directory (AD) service authenticates users and devices in a Windows or UNIX-based domain network, and verifies permissions to determine the user access level at log in.
Add an LDAP/AD Provider
You must configure providers in OT Link Platform to activate this type of authentication. The OT Link Platform device contains a client that communicates with the LDAP server and receives information based on the client access level.
- OT Link Platform Authentication Providers do not support nested groups. Create a separate group for each OT Link Platform role in the LDAP Registry, and add users to these groups.
- Once you have added a provider, you need to select a provider on the OT Link Platform login screen.
- OT Link Platform should always have at least one administrator user. LDAP administrator users can meet this requirement.
To add an LDAP/AD provider:
-
In the OT Link Platform navigation panel, choose System > LDAP/AD Auth.
- Click
 to launch the Add Provider dialog.
to launch the Add Provider dialog. - Enter the configuration details, as described in LDAP Provider Details. Click Create.
LDAP Provider Details
For more information on LDAP / AD providers, see the following section. Use this guide to configure LDAP / AD with OT Link Platform.
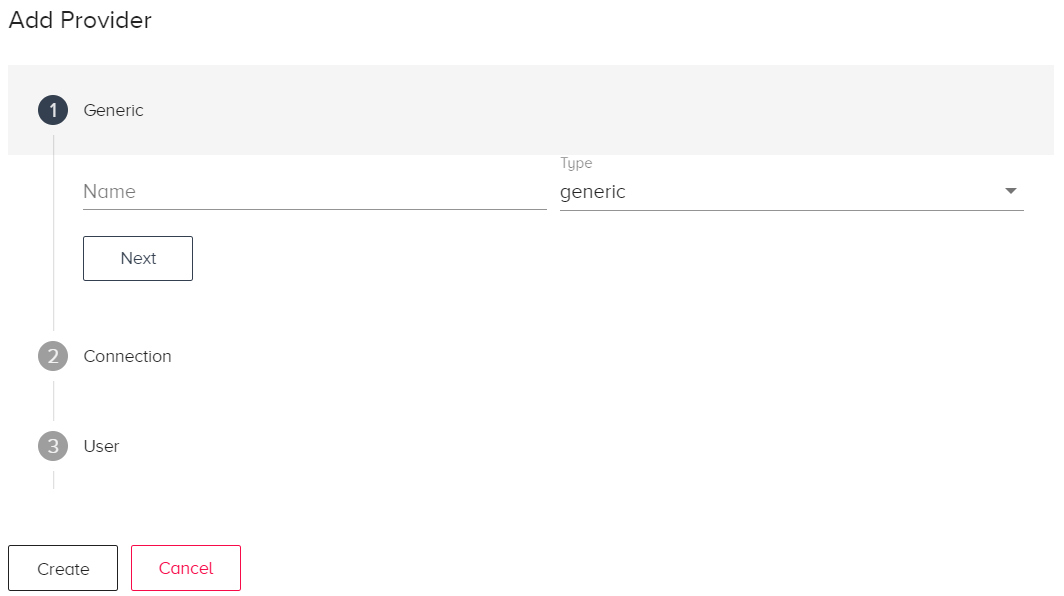
General Settings
Name: Enter a user-defined name.
Type: Currently only generic is valid.
Find LDAP Distinguished Names (DN)
To configure LDAP for OT Link Platform, you must have the DN information from the LDAP server.
Bind DN
An LDAP Bind DN supplies the user and the user location in the LDAP directory tree. The LDAP client configuration file contains this information. You can access it in the following directory:
/etc/ldap.conf
To find the Bind DN:
- Log in to the Windows server connected to the Active Directory.
- Identify the domain to query.
-
At the Windows command prompt, type the following command to retrieve a specific user.
dsquery user dc=<domain_name>,dc=<domain_extension> -name <user_name>Command Info:
dc means domain component or context
: Replace this with your domain name, without the extension : Replace this with your domain's extension, like .com : Replace this with the user name to search. -
To retrieve all users, enter the following into the command prompt:
dsquery user dc=<domain_name>,dc=<domain_extension>
Connection Settings
Host: Enter the hostname, the fully qualified domain name or IP address, of your LDAP server.
Port: Enter the LDAP host port number. The default LDAPS (Secure LDAP) port is 636; the default LDAP port is 389.
TLS: Check this box to indicate that you want to use LDAP over Transport Layer Security (TLS) to authenticate Active Directory sessions. The TLS protocol provides authentication and data encryption between servers and applications on a network. Note: When this box is not checked, OT Link Platform expects to find a configured Custom Certificate.
TLSRootCA: Enter the root SSL/TLS certificate.
Sample Certificate:
Make sure to include —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—– when entering the certificate. See the following example for a sample certificate:
—–BEGIN CERTIFICATE—–
MIIFOjCCAyKgAwIBAgIBATANBgkqhkiG9w0BAQsFADBAMRowGAYDVQQKExFMaXRt
—–END CERTIFICATE—–
Bind DN: The bind DN identifies the user and the location of the user in the LDAP directory tree. In the following example: CN=common name, OU=organizational unit, and DC=domain component.
CN = user1, CN = Users, DC = examplecompany, DC = com
CN = Manager, OU = IT, DC = examplecompany, DC = com
See Find the LDAP Bind DN.
Bind DN Password: Enter the DN (distinguished name) password.

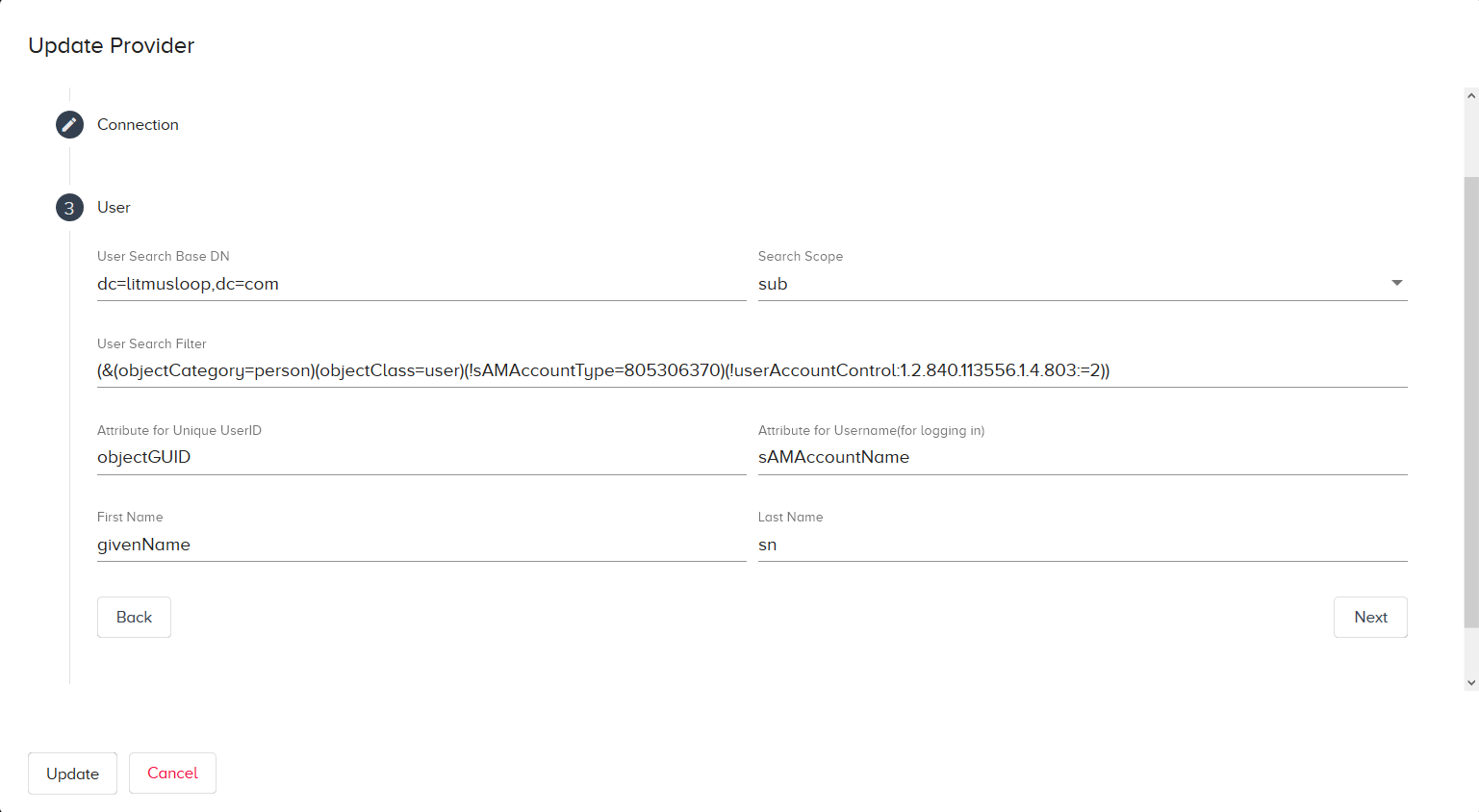
LDAP User Settings
User Search Base DN: This Base DN (Distinguished Name) is the point in the LDAP directory tree that the LDAP service uses to initiate a user search. The Base DN is the latter part of the Bind DN. See Find the LDAP Bind DN.
Search Scope: Select one of the following: base, one, sub. Base limits the search to the base object. One restricts the search to “one level” or in other words, the immediate children of the base object. Sub enables a full LDAP tree search, including all children of the base object.
User Search Filter: Enter a filter to search LDAP users.
Attribute for Unique UserID: Enter the unique user ID number (uidNumber).
Attribute for Username: Enter the unique user ID (uid).
First Name: Enter the given name of the user.
Last Name: Enter the surname of the user.
Group Settings
User Groups
You must define the following groups on the LDAP / AD server to have users with different permissions in OT Link Platform:
OT Link Platform-administrator : Full access to all features and all system configuration settings.
OT Link Platform-developer : Can view OT Link Platform and use all of its features. Developers cannot alter the system configuration.
OT Link Platform-observer : Only views OT Link Platform and cannot use any features, such as adding devices and tags. Observers cannot make any configuration changes.
LDIF Info:
The LDAP LDIF (LDAP Interchange Format) file can define attributes, such as user access control permissions. The following example shows the LDIF format for the mydom organization.
dn: cn = employees, ou = Groups, dc = mydom, dc = com
changetype: modify
add: memberUid
memberUid: arc815
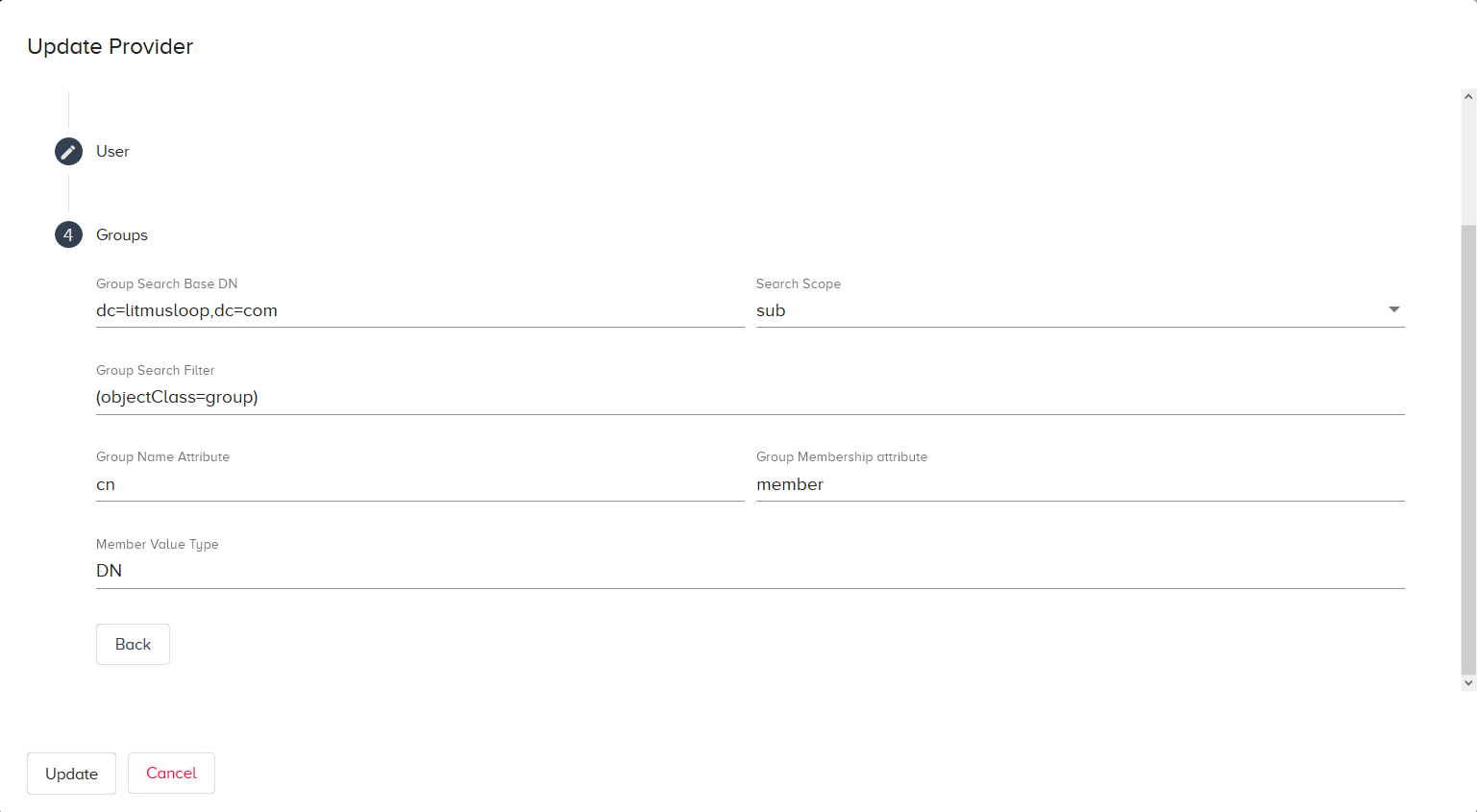
Group Search Base DN: This Base DN (Distinguished Name) is the starting point that the LDAP service uses to find a group in the LDAP directory tree.
Example of a Group Base DN:
CN=Users,CN=Builtin,DC=MyDomain,DC=com
Search Scope: Select one of the following: base, one, sub. Base limits the search to the base object. One restricts the search to “one level”, as in the immediate children of the base object. Sub enables a full LDAP tree search, including all children of the base object
Group Search Filter: Enter a filter to query the Active Directory. Click here for a reference to help guide you in creating search filters.
Example of a filter to query group objects with a common name (CN) starting with Admin:
(&(objectCategory=group)(cn=Admin*))
Group Name Attribute: Enter the common name (CN) for the group to search.
Group Membership Attribute: Enter the distinguished name (DN) for the group to search.
Member Value Type: Enter the value type for members in the group, DN or CN
Log In with Authentication
After configuring LDAP, users must select a Provider ID when they log in to OT Link Platform.
The Username is from the LDAP server. The Password must match the Bind DN Password from the configuration.

The Internal authentication provider appears in the ID selection list. If you do not select another ID, OT Link Platform uses this non-configurable, default provider ID.